Twisted Panda: The Chinese Hackers
The attacks, dubbed “Twisted Panda,” coincide with Russia’s military invasion of Ukraine, enabling a wide range of threat actors to quickly alter their campaigns to distribute malware and perform opportunistic attacks in response to the current conflict.
They’ve taken the shape of social engineering methods with topical conflict and sanctions baits designed to dupe potential victims into clicking illegal links or opening weaponized documents. Check Point, an Israeli cybersecurity company, linked the current intelligence-gathering activity to a Chinese threat actor with ties to Stone Panda (also known as APT 10, Cicada, or Potassium) and Mustang Panda (aka Bronze President, HoneyMyte, or RedDelta). The action is believed to be a continuation of “a long-running espionage campaign against Russian-related companies that has been in existence since at least June 2021,” with the most recent indications of it being discovered in April 2022.
Target Companies
Two defence research organizations belonging to the Russian state-owned defence company Rostec Corporation and an unknown entity in Minsk, Belarus, were among the targets.
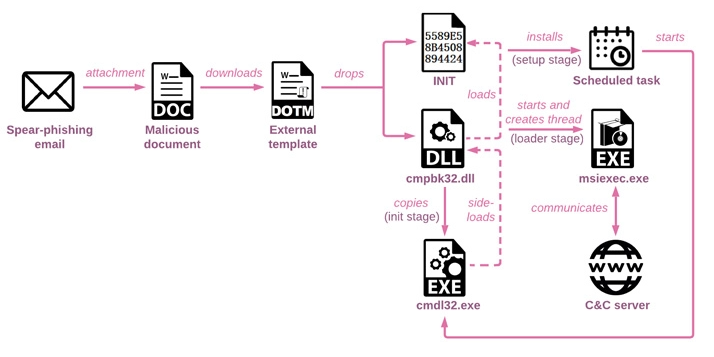
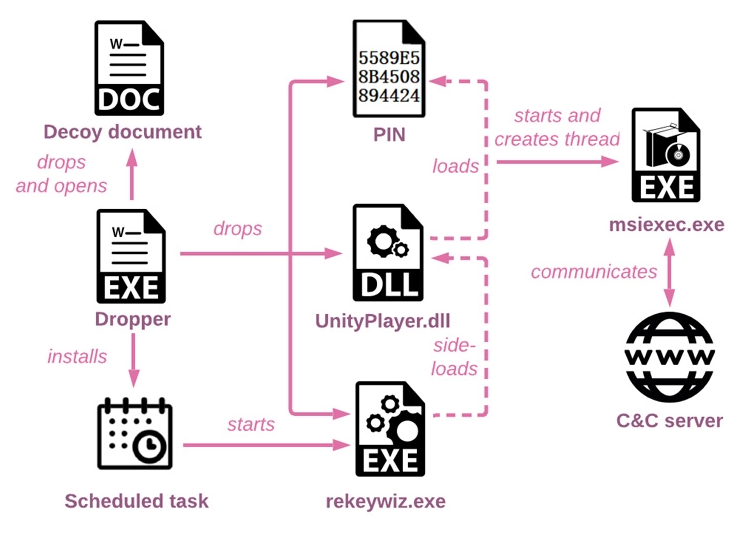
The phishing attempts began with emails including a fake Microsoft Word document meant to activate the infection and drop a loader, posing as the Russian Ministry of Health but actually being an attacker-controlled website. Apart from establishing persistence via a scheduled task, the 32-bit DLL (“cmpbk32.dll”) can run a second-stage multi-layered loader, which is then unpacked to run the final payload in memory. The injected payload, Spinner, is a previously unknown backdoor that employs advanced techniques like control flow flattening to hide the program flow, which has previously been identified as being used by both Stone Panda and Mustang Panda in their attacks. Also read: Government Employees can get Online salary slips with PIFRA